Analyzing ATM Malwares
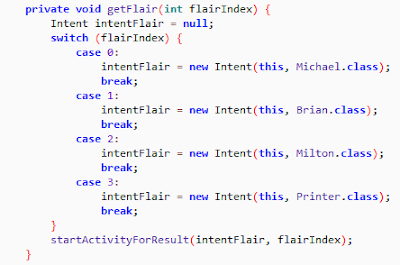
This post will explain how to analyze ATM malwares developed using middle ware CEN/XFS (extension for financial services). ATM (Automated Teller machine). The three leading ATM vendors are - 1.NCR 2.Diebold 3.Wincor The main services (peripherals) of an ATM are - 1.Card Reader 2.PinPad 3.Cash Dispenser Applications developed to interact with ATM services (peripherals) uses CEN/XFS (extension for financial services). XFS provides the API to access and manipulate the ATM peripherals from different vendors as shown in below image. CEN/XFS Application Programming interface and SDK can be downloaded from below website under Published CWA's. https://www.cen.eu/work/areas/ICT/eBusiness/Pages/WS-XFS.aspx Apart from CEN/XFS Application Programming interface and SDK other important guides as mentioned below and can be download from above mentioned website. 1.Service Class Definition - Programmer's Reference 2.Identification Card Device Class Interface - Programmer...