FireEye FLARE CTF 2017 : APK Challenge 8
The challenge required decrypting passwords in order to form AES key to decrypt the flag bytes.
On decompiling flair.apk file we can see four classes for which we need to decrypt passwords.
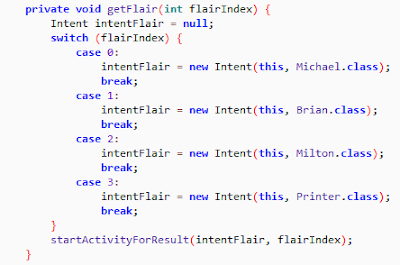

2. Brian Class
Password is formed as shown below.
String.format("%s_%s%x_%s!", new Object[]{t, y, Integer.valueOf(p), c});
t = (ImageView) findViewById(R.id.pfdu).getTag().toString()
y = getApplicationContext().getPackageManager().getApplicationInfo(getApplicationContext().getPackageName(), 128).metaData.getString("vdf")
p = (TextView) findViewById(R.id.vcxv).getCurrentTextColor() & SupportMenu.USER_MASK;
c = (TextView) findViewById(R.id.vcxv).getText().toString().split(" ")[4];
The Password is hashtag_covfefe_Fajitas!.

3.Milton Class
The password is formed by decrypting a string and taking SHA1 of the decrypted string.

Decryption algorithm used are base64, xor and substitution operation.
I wrote python script to decrypt password string for Milton Class.
Output of above python script.
Milton Class String ---> A rich man is nothing but a poor man with money.
Milton Class String SHA1 ---> 10aea594831e0b42b956c578ef9a6d44ee39938d
4.Printer Class
To get password for printer class we need to decrypt few strings to understand what below function is doing.

The string in above function can be decrypted by passing them to above python script as shown below.

Decrypted strings as shown below.
JT43W0c= ---> SHA-1
Gv@H --> tspe
,e}e8yGS!8Dev)-e@ --> java.util.HashMap
vSBH --> size
LHG --> get
H?ye!v --> equals
,e}e8yGS!81PPe(v --> java.util.Arrays
,e}e8S98*eGeu.@yG5GPHed --> java.io.DataInputStream
e.RP9SR8x9.GH.G8PHv81vvHG-e.eLHP --> android.content.res.AssetManager
9@H. --> open
PHeR --> read
PHeRu.G --> readInt
,e}e8yGS!8Dev)-e@ --> java.util.HashMap
@yG --> put
PHeR"(GH --> readByte
PHeR5)9PG --> readShort
e.RP9SR8x9.GH.G8M9.GHkG --> android.content.Context
e.RP9SR8x9.GH.G8@d81@@!SxeGS9.u.g9 --> android.content.pm.ApplicationInfo
g!eLv --> flags
LHG1@@!SxeGS9.u.g9 --> getApplicationInfo
LHG1@@!SxeGS9.M9.GHkG --> getApplicationContext
Function is reading tspe file from asset folder and forming password string.

Printer Class Decrypted String : Give a man a fire and he'll be warm for a day. Set a man on fire and he'll be warm for the rest of his life.
Printer Class Decrypted String SHA1 : 5f1be3c9b081c40ddfc4a0238156008ee71e24a4
Once we get password for all four classes we need to concatenate passwords to form AES key and decrypt flag bytes.

Flag : pc_lo4d_l3tt3r_gl1tch@flare-on.com
On decompiling flair.apk file we can see four classes for which we need to decrypt passwords.

1.Michael Class
It was pretty simple password comparison.The password is MYPRSHE__FTW.

Password is formed as shown below.
String.format("%s_%s%x_%s!", new Object[]{t, y, Integer.valueOf(p), c});
t = (ImageView) findViewById(R.id.pfdu).getTag().toString()
y = getApplicationContext().getPackageManager().getApplicationInfo(getApplicationContext().getPackageName(), 128).metaData.getString("vdf")
p = (TextView) findViewById(R.id.vcxv).getCurrentTextColor() & SupportMenu.USER_MASK;
c = (TextView) findViewById(R.id.vcxv).getText().toString().split(" ")[4];
The Password is hashtag_covfefe_Fajitas!.

3.Milton Class
The password is formed by decrypting a string and taking SHA1 of the decrypted string.

Decryption algorithm used are base64, xor and substitution operation.
I wrote python script to decrypt password string for Milton Class.
Output of above python script.
Milton Class String ---> A rich man is nothing but a poor man with money.
Milton Class String SHA1 ---> 10aea594831e0b42b956c578ef9a6d44ee39938d
4.Printer Class
To get password for printer class we need to decrypt few strings to understand what below function is doing.

The string in above function can be decrypted by passing them to above python script as shown below.

Decrypted strings as shown below.
JT43W0c= ---> SHA-1
Gv@H --> tspe
,e}e8yGS!8Dev)-e@ --> java.util.HashMap
vSBH --> size
LHG --> get
H?ye!v --> equals
,e}e8yGS!81PPe(v --> java.util.Arrays
,e}e8S98*eGeu.@yG5GPHed --> java.io.DataInputStream
e.RP9SR8x9.GH.G8PHv81vvHG-e.eLHP --> android.content.res.AssetManager
9@H. --> open
PHeR --> read
PHeRu.G --> readInt
,e}e8yGS!8Dev)-e@ --> java.util.HashMap
@yG --> put
PHeR"(GH --> readByte
PHeR5)9PG --> readShort
e.RP9SR8x9.GH.G8M9.GHkG --> android.content.Context
e.RP9SR8x9.GH.G8@d81@@!SxeGS9.u.g9 --> android.content.pm.ApplicationInfo
g!eLv --> flags
LHG1@@!SxeGS9.u.g9 --> getApplicationInfo
LHG1@@!SxeGS9.M9.GHkG --> getApplicationContext
Function is reading tspe file from asset folder and forming password string.

Printer Class Decrypted String SHA1 : 5f1be3c9b081c40ddfc4a0238156008ee71e24a4
Once we get password for all four classes we need to concatenate passwords to form AES key and decrypt flag bytes.

Flag : pc_lo4d_l3tt3r_gl1tch@flare-on.com


ReplyDeleteBEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE….. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . ………. EXPLANATION OF HOW THESE CARD WORKS………. You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $1,000, 2nd VAULT $2,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly… Done. ***NOTE: DON’T EVER MAKE THE MISTAKE OF CLICKING THE “ALL” OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com) We are located in USA.
**Contact 24/7**
DeleteTelegram > @killhacks
ICQ > 752822040
Skype > Peeterhacks
Wicker me > peeterhacks
**HIGH CREDIT SCORES SSN FULLZ AVAILABLE**
>For tax filling/return
>SSN DOB DL all info included
>For SBA & PUA
>Fresh spammed & Fresh database
**TOOLS & TUTORIALS AVAILABLE FOR HACKING SPAMMING
CARDING CASHOUT CLONING SCRIPTING**
Fullz info included
NAME+SSN+DOB+DL+DL-STATE+ADDRESS
Employee & Bank details included
High credit fullz with DL 700+
(bulk order preferable)
**Payment in all crypto currencies will be accepted**
->You can buy few for testing
->Invalid or wrong info will be replaced
->Serious buyers contact me for long term business & excellent profit
->Genuine & Verified stuff
TOOLS & TUTORIALS AVAILABLE:
"SPAMMING" "HACKING" "CARDING" "CASH OUT"
"KALI LINUX" "BLOCKCHAIN BLUE PRINTS" "SCRIPTING"
**TOOLS & TUTORIALS LIST**
=>US CC Fullz
=>Ethical Hacking Tools & Tutorials
=>Bitcoin Hacking
=>Kali Linux
=>Keylogger & Keystroke Logger
=>Bulk SMS Sender
=>Facebook & Google Hacking
=>Bitcoin Flasher
=>SQL Injector
=>Logins Premium (PayPal/Amazon/Coinbase/Netflix/FedEx/Banks)
=>Bitcoin Cracker
=>SMTP Linux Root
=>Shell Scripting
=>DUMPS with pins track 1 and 2 with & without pin
=>SMTP's, Safe Socks, Rdp's brute
=>PHP mailer
=>SMS Sender & Email Blaster
=>Cpanel
=>Server I.P's & Proxies
=>Viruses & VPN's
=>HQ Email Combo (Gmail, Yahoo, Hotmail, MSN, AOL, etc)
==>Contact 24/7<==
Telegram> @killhacks
ICQ> 752822040
Skype> Peeterhacks
Wicker me > peeterhacks
*Serious buyers are always welcome
*Big Discount in bulk order
*Offer gives monthly, quarterly, half yearly & yearly
*Hope we do a great business together
**You should try at least once**
We have been using Mr Benjamin financial team to help secure our first acreage block. We are happy with the professionalism In Financial Services Mr Benjamin and his loan company brings to the table with the loan rate of 2% interest rate that we use to get our loan from Mr Benjamin we are also doing a separate construction loan with them. Everything has been a breeze with the team behind Mr Benjamin which is 100% of the way, and no question is too silly to ask. Would recommend this Loan officer to anyone looking for a loan at the low rate of 2% RIO!! Email Mr Benjamin and his team today for any kind of loan 247officedept@gmail.com Whats-App Number +1-989-394-3740
ReplyDeletePLEASE READ!!Hello Guys!!!I am Caro I live in Ohio USA I’m 32 Years old, am so happy I got my blank ATM card from Adriano. My blank ATM card can withdraw $4,000 daily. I got it from Him last week and now I have withdrawn about $10,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it because it is blank just your PIN will be on it, it is not traceable and now I have money for business, shopping and enough money for me and my family to live on.I am really glad and happy i met Adriano because I met Five persons before him and they could not help me. But am happy now Adriano sent the card through DHL and I got it in two days. Get your own card from him right now, he is giving it out for small fee to help people even if it is illegal but it helps a lot and no one ever gets caught or traced. I’m happy and grateful to Adriano because he changed my story all of a sudden. The card works in all countries that is the good news Adriano’s email address is adrianohackers01@gmail.com.
ReplyDeletePLEASE READ!!Hello Guys!!!I am Caro I live in Ohio USA I’m 32 Years old, am so happy I got my blank ATM card from Adriano. My blank ATM card can withdraw $4,000 daily. I got it from Him last week and now I have withdrawn about $10,000 for free. The blank ATM withdraws money from any ATM machines and there is no name on it because it is blank just your PIN will be on it, it is not traceable and now I have money for business, shopping and enough money for me and my family to live on.I am really glad and happy i met Adriano because I met Five persons before him and they could not help me. But am happy now Adriano sent the card through DHL and I got it in two days. Get your own card from him right now, he is giving it out for small fee to help people even if it is illegal but it helps a lot and no one ever gets caught or traced. I’m happy and grateful to Adriano because he changed my story all of a sudden. The card works in all countries that is the good news Adriano’s email address is adrianohackers01@gmail.com.
ReplyDelete**SELLING SSN+DOB FULLZ**
ReplyDeleteCONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
>>1$ each without DL/ID number
>>2$ each with DL
>>5$ each for premium (also included relative info)
*Will reduce price if buying in bulk
*Hope for a long term business
FORMAT OF LEADS/FULLZ/PROS
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->COMPLETE ADDRESS
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYMENT DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>Fresh Leads for tax returns & w-2 form filling
>Payment mode BTC, ETH, LTC, PayPal, USDT & PERFECT MONEY
''OTHER GADGETS PROVIDING''
>SSN+DOB Fullz
>CC with CVV
>Photo ID's
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>HQ Emails with passwords
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
THANK YOU
DO YOU NEED A PERSONAL/BUSINESS/INVESTMENT LOAN? CONTACT US TODAY VIA WhatsApp +19292227023 Email drbenjaminfinance@gmail.com
ReplyDeleteHELLO
Loan Offer Alert For Everyone! Are you financially down and you need an urgent credit/financial assistance? Or are you in need of a loan to start-up/increase your business or buy your dream house. Are you in search of a legit loan? Tired of Seeking Loans and Mortgages? Have you been turned down by your banks? Have you also been scammed once? Have you lost money to scammers or to Binary Options and Cryptocurrency Trading, We will help you recover your lost money and stolen bitcoin by our security FinanceRecovery Team 100% secured, If you are in financial pains consider your financial trauma over. We Offer LOANS from $3,000.00 Min. to $30,000,000.00 Max. at 2% interest rate NO MATTER YOUR CREDIT SCORE. GET YOUR INSTANT LOAN APPROVAL 100% GUARANTEED TODAY VIA WhatsApp:+19292227023 Email: drbenjaminfinance@gmail.com
Hello everyone, Are you looking for a professional trader, forex and binary manager who will help you trade and manager your account with good and massive amount of profit in return. you can contact Mr. Anderson for your investment plan, for he helped me earned 8,000usd with little investment funds. Mr Anderson you're the best trader I can recommend for anyone who wants to invest and trade with a genuine trader, he also helps in recovery of loss funds..you can contact him on his whatsapp: (+447883246472) Email (tdameritrade077@gmail.com)I advice you shouldn't hesitate He's great.
ReplyDeleteHi,
ReplyDeleteThanks for Sharing a very useful information on Fireeye Flare CTF. Keep it up such a nice posting like this.
Regards,
SAM Web Studio
Web Development Services in Delhi
Bardzo fajny sklep internetowy z lutownicami super ceny
ReplyDeleteNajlepszy sklep super asortyment oraz super ceny
Lutownica transformatorowa
Lutownica transformatorowa
Lutownica transformatorowa
Lutownica transformatorowa
I had to leave this post here as a sign of gratitude since that is one of the least BRIXTON asked of me. From my calculations, I made $25,200 in 1-week trading but unfortunately lost it all after I tried to participate in an airdrop, I became very devastated until I read some wonderful reviews about WIZARD BRIXTON. I feel so much joy right now because BRIXTON did come through for me by getting my money back from those scam artists, my advice is for you to be mindful of the links you click online to avoid losing your money. The experience of losing your money to a scammer is not funny no matter how much. Feel free to ask me more hanswilton3@gmail.com or contact WIZARD BRIXTON via
ReplyDeleteEMAIL : WIZARDBRIXTON(AT) GMAIL (DOT) COM
WHATS-APPS : (+1- /807-23 ) 4-0428
Fullz (CC, CVV, High CS, EIN Business, etc)
ReplyDeleteTools (Carding, Spamming, Hacking, Penetration, etc)
Tutorials (Filling, SBA, Carding, CAshout, Dumps Cash out, etc)
Scam Pages (FB, E-Bay, Spotify, Amazon, etc)
Dumps (Track 101 & 202 Pins/without Pins)
Mailers (PHP, SMTP, alxus, web mailer, etc)
Senders
Leads/Pros (SSN DOB, SSN DOB DL, Employement, etc)
Dead Fullz
Viruses (RAT's, Key-loggers, etc)
Kali Linux Complete
All legit stuff Available at cheap Prices
Guidance will be provided if needed
Contact for more info
@killhacks ' TG/icq
peeterhacks ' Skype/Wickr
Mail ' exploit(dot)tools4u at gmail (dot)com
it is quite an interesting topic to debate. Well, if you are looking for a chance for any home improvements then visit us at Lowes.com/survey
ReplyDeleteThis is definitely an engaging topic for discussion. If you're looking for reliable help with tax filing, feel free to check us out at Installtubotax.com. we make tax season simpler with easy-to-use tools and expert support.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteYou've really broadened my perspective on this topic with insightful and well-grounded information.If you’re interested in sharing your recent shopping experience and entering to win exciting rewards, be sure to visit PublixSurvey.com
ReplyDeletecoinbase customer service phone number does offer customer support by phone, but access is limited and usually focused on account security issues such as unauthorized activity. Unlike traditional banks, Coinbase relies more heavily on online support tools.
ReplyDelete