FireEye FLARE CTF 2017 : APK Challenge 8
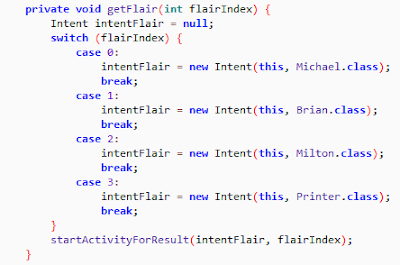
The challenge required decrypting passwords in order to form AES key to decrypt the flag bytes. On decompiling flair.apk file we can see four classes for which we need to decrypt passwords. 1.Michael Class It was pretty simple password comparison.The password is MYPRSHE__FTW . 2. Brian Class Password is formed as shown below. String.format("%s_%s%x_%s!", new Object[]{t, y, Integer.valueOf(p), c}); t = (ImageView) findViewById(R.id.pfdu).getTag().toString() y = getApplicationContext().getPackageManager().getApplicationInfo(getApplicationContext().getPackageName(), 128).metaData.getString("vdf") p = (TextView) findViewById(R.id.vcxv).getCurrentTextColor() & SupportMenu.USER_MASK; c = (TextView) findViewById(R.id.vcxv).getText().toString().split(" ")[4]; The Password is hashtag_covfefe_Fajitas! . 3.Milton Class The password is formed by decrypting a string and taking SHA1 of the decrypted string. Decryption algorithm

