Memory Forensics : Tracking Process Injection
This post describe about process memory internals which allow us to track process injections.
Example used below is recent Brazil Malspam (hxxp://malware-traffic-analysis.net/2017/07/07/index.html) which inject DLL fltLib.dll into process notepad.exe.
Attach kernel debugger to infected machine and get information about notepad.exe Process object.
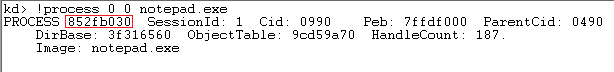
Process object is represented by EPROCESS structure. VAD (Virtual Address Descriptors) is member of EPROCESS structure and describes the layout of process memory segments. VADs contain the names of memory-mapped files, the total number of pages in the region, the initial protection (read, write, execute), and several other flags that can tell you a lot about what type of data the regions contain.

VAD is a self balancing tree and each node in tree represent one range in process virtual memory.Each node has child in the form of left and right node.A node is represented using MMADDRESS_NODE structure.

Listing all VAD nodes of notepad.exe using Parent node address 0x852fb2a8.

start and end are VPN (Virtual Page Numbers). Describe the range of virtual memory for node.
commit - Number of pages commited.
Protection - EXECUTE_WRITECOPY. Enables execute, read-only, or copy-on-write access to a
mapped view of a file. DLL's have this kind of protection.
Let's see how we can derive virtual memory address from VPN's of node. We will also see structures which store commit, Protection values for a node and also track down the object representing mapped fltLib.dll.
As mentioned above each node is represented by MMADDRESS_NODE. Let's have a look at node (0x8539de90) containing injected fltLib.dll.

To convert a page number to virtual memory address, multiply page number with page size.

As shown above VPN*PageSize = 0x2a40*0x1000 = 0x2a40000. Dumping 2 bytes at memory address 0x2a40000 we get 'MZ' portable executable magic bytes which means fltLib.dll is loaded at memory address 0x2a40000.
We can confirm the above findings by switching to user mode to view loaded module in process notepad.exe.

Below are the loaded modules in process notepad.exe .Virtual address of fltLib.dll is 0x2a4000 as highlighted below.

Starting windows Vista till windows 7 VAD's node is represented using MMADDRESS_NODE structure. In Windows XP VAD's node is represented using MMVAD structure.
Representing node (0x8539de90) contains fltLib.dll using MMVAD structure.As we can see in below image MMVAD structure contains a union u which have two members LongFlags and VadFlags.
Below is representation of bits of VadFlags.
dt nt!_MMVAD_FLAGS
+0x000 CommitCharge : Pos 0, 19 Bits
+0x000 NoChange : Pos 19, 1 Bit
+0x000 VadType : Pos 20, 3 Bits
+0x000 MemCommit : Pos 23, 1 Bit
+0x000 Protection : Pos 24, 5 Bits
+0x000 Spare : Pos 29, 2 Bits
+0x000 PrivateMemory : Pos 31, 1 Bit
CommitCharge - specifies the number of pages committed in the region described by the VAD node.
Protection - This field indicates what type of access should be allowed to the memory region.
// Protection bits:
#define MM_ZERO_ACCESS 0 // this value is not used.
#define MM_READONLY 1
#define MM_EXECUTE 2
#define MM_EXECUTE_READ 3
#define MM_READWRITE 4 // bit 2 is set if this is writable.
#define MM_WRITECOPY 5
#define MM_EXECUTE_READWRITE 6
#define MM_EXECUTE_WRITECOPY 7
VadType
Tag Node Type
Vadl _MMVAD_LONG
Vadm _MMVAD_LONG
Vad _MMVAD_LONG
VadS _MMVAD_SHORT
VadF _MMVAD_SHORT

VadType is defined by PoolTag member of POOL_HEADER structure which exists in memory directly before the node address.
Subtracting the size of POOL_HEADER structure from address (0x8539de90) of node contains fltLib.dll to get address of POOL_HEADER structure.


To track the object representing fltLib.dll, we need to look at SUBSECTION structure which OS uses to track information on files or DLLs mapped into the region.
SUBSECTION structure is member of MMVAD structure and is at offset 0x24. Below is the SUBSECTION structure for node address 0x8539de90.

SUBSECTION structure contains CONTROL_AREA structure as one of its member.Below is the CONTROL_AREA structure.

CONTROL_AREA structure member FilePointer points to another structure _EX_FAST_REF which contains pointer to object representing fltLib.dll.

Object member of _EX_FAST_REF structure point to file object (_FILE_OBJECT) structure representing fltLib.dll.
To get address of _FILE_OBJECT structure we have to mask the value of Object member of _EX_FAST_REF with 0xfffffff8 as shown below.

file security
ReplyDeleteAdd file access control and file IOs monitor to your windows application with Windows file system mini filter driver component in C#, C++ demo source code to implement your file security solution
http://easefilter.com/
I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com or whatsapp: +1(213)785-1553
ReplyDelete
ReplyDeleteBEST WAY TO HAVE GOOD AMOUNT TO START A GOOD BUSINESS or TO START LIVING A GOOD LIFE….. Hack and take money directly from any ATM Machine Vault with the use of ATM Programmed Card which runs in automatic mode. email (williamshackers@hotmail.com) for how to get it and its cost . ………. EXPLANATION OF HOW THESE CARD WORKS………. You just slot in these card into any ATM Machine and it will automatically bring up a MENU of 1st VAULT $1,000, 2nd VAULT $2,000, RE-PROGRAMMED, EXIT, CANCEL. Just click on either of the VAULTS, and it will take you to another SUB-MENU of ALL, OTHERS, EXIT, CANCEL. Just click on others and type in the amount you wish to withdraw from the ATM and you have it cashed instantly… Done. ***NOTE: DON’T EVER MAKE THE MISTAKE OF CLICKING THE “ALL” OPTION. BECAUSE IT WILL TAKE OUT ALL THE AMOUNT OF THE SELECTED VAULT. email (williamshackers@hotmail.com) We are located in USA.
Do you need Personal Finance?
ReplyDeleteBusiness Cash Finance?
Unsecured Finance
Fast and Simple Finance?
Quick Application Process?
Finance. Services Rendered include,
*Debt Consolidation Finance
*Business Finance Services
*Personal Finance services Help
contact us today and get the best lending service
personal cash business cash just email us below
Contact Us: financialserviceoffer876@gmail.com
call or add us on what's app +918929509036
i was lost with no hope for my wife was cheating and had always got away with it because i did not know how or
ReplyDeletealways too scared to pin anything on her. with the help a friend who recommended me to who help hack her phone,
email, chat, sms and expose her for a cheater she is. I just want to say a big thank you to
SUPERIOR.HACK@GMAIL.COM . am sure someone out there is looking for how to solve his relationship problems, you can also contact him for all sorts of hacking job..he is fast and reliable. you could also text +1 213-295-1376(whatsapp) contact and thank me later
Hi Guy's
ReplyDeleteFresh & valid spammed USA SSN+Dob Leads with DL available in bulk.
>>1$ each SSN+DOB
>>2$ each with SSN+DOB+DL
>>5$ each for premium (also included relative info)
Prices are negotiable in bulk order
Serious buyer contact me no time wasters please
Bulk order will be preferable
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
OTHER STUFF YOU CAN GET
SSN+DOB Fullz
CC's with CVV's (vbv & non-vbv)
USA Photo ID'S (Front & back)
All type of tutorials available
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SMTP Linux Root
DUMPS with pins track 1 and 2
Socks, rdp's, vpn's
Server I.P's
HQ Emails with passwords
Looking for long term business
For trust full vendor, feel free to contact
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
DO YOU NEED A PERSONAL/BUSINESS/INVESTMENT LOAN? CONTACT US TODAY VIA WhatsApp +19292227023 Email drbenjaminfinance@gmail.com
ReplyDeleteHELLO
Loan Offer Alert For Everyone! Are you financially down and you need an urgent credit/financial assistance? Or are you in need of a loan to start-up/increase your business or buy your dream house. Are you in search of a legit loan? Tired of Seeking Loans and Mortgages? Have you been turned down by your banks? Have you also been scammed once? Have you lost money to scammers or to Binary Options and Cryptocurrency Trading, We will help you recover your lost money and stolen bitcoin by our security FinanceRecovery Team 100% secured, If you are in financial pains consider your financial trauma over. We Offer LOANS from $3,000.00 Min. to $30,000,000.00 Max. at 2% interest rate NO MATTER YOUR CREDIT SCORE. GET YOUR INSTANT LOAN APPROVAL 100% GUARANTEED TODAY VIA WhatsApp:+19292227023 Email: drbenjaminfinance@gmail.com
FULLZ AVAILABLE
ReplyDeleteFresh & valid spammed USA SSN+Dob Leads with DL available in bulk.
>>1$ each SSN+DOB
>>3$ each with SSN+DOB+DL
>>5$ each for premium fullz (700+ credit score with replacement guarantee)
Prices are negotiable in bulk order
Serious buyer contact me no time wasters please
Bulk order will be preferable
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
OTHER STUFF YOU CAN GET
SSN+DOB Fullz
CC's with CVV's (vbv & non-vbv)
USA Photo ID'S (Front & back)
All type of tutorials available
(Carding, spamming, hacking, scam page, Cash outs, dumps cash outs)
SMTP Linux Root
DUMPS with pins track 1 and 2
WU & Bank transfers
Socks, rdp's, vpn
Php mailer
Sql injector
Bitcoin cracker
Server I.P's
HQ Emails with passwords
All types of tools & tutorials.. & much more
Looking for long term business
For trust full vendor, feel free to contact
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
Excellent post. I've been browsing this blog constantly thanks for sharing
ReplyDeletevstcomplex
Goodhertz Vulf Crack
4Front TruePianos Crack
Arturia Pigments Crack
XSplit VCam Crack
AMEK EQ Crack
MusicLab RealEight Crack
WiFi Explorer Pro Crack
Fullz/Leads/Pros
ReplyDeleteSSN+DOB+DL Full/Pros
High Cresdit Scores Fullz
CC With CVV Fullz
Dumps With Pin & Without Pin Codes
Business EIN Fullz
Fullz for Tax Return Filling
SBA/PUA/UI Filling Fullz
Premium Fullz For applying loans
Bulk quantity fullz available
Fresh Spammed & Genuine stuff
Fastest Delivery within Mins
Invalid stuff will be replaced
For Contact:
@killhacks - Telegram/ICQ
@peeterhacks - Wickr/Skype
Hacking, Carding, Spamming, Cracking Tools&Tutorials available too
Mailers/Senders/C-panels/Shells/Web-mailers
Brutes/Dorks/RAT's/RDP's/Viruses
Fr**d Bi**e 2021/2022
Kali Linux/Python Full
Keyloggers/WA.FB Hacking Methods
Full Packages are also available
For More Info:
@leadsupplier - TG
752822040 - ICQ
@peeterhacks - Wickr/Skype