DoublePulsar Backdoor

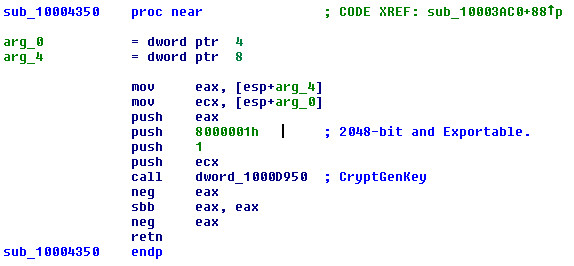
This post explains DoublePulsar Backdoor and how WannaCry Ransomware uses it to spread Itself. EternalBlue Installing DoublePulasr Backdoor EternalBlue exploits vulnerability in SMB protocol and execute shell code.Offset of shell code in EternalBlue binary that is present in shadow broker dump. Shellcode finds address of srv.sys (SMB Driver) and replace address of srv!SrvTransactionNotImplemented function in srv!SrvTransaction2DispatchTable with its own function address as shown below. Offset of function code in EternalBlue binary which replaces srv!SrvTransactionNotImplemented function address in srv!SrvTransaction2DispatchTable . Before overwriting srv!SrvTransactionNotImplemented function in srv!SrvTransaction2DispatchTable with its own function address shell code allocates memory using ExAllocatePool API and write function bytes. Function code is stored at 0x48 offset from memory addres...