Memory Forensics : Tracking Process Injection
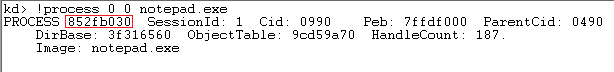
This post describe about process memory internals which allow us to track process injections. Example used below is recent Brazil Malspam (hxxp://malware-traffic-analysis.net/2017/07/07/index.html) which inject DLL fltLib.dll into process notepad.exe. Attach kernel debugger to infected machine and get information about notepad.exe Process object. Process object is represented by EPROCESS structure. VAD (Virtual Address Descriptors) is member of EPROCESS structure and describes the layout of process memory segments. VADs contain the names of memory-mapped files, the total number of pages in the region, the initial protection (read, write, execute), and several other flags that can tell you a lot about what type of data the regions contain. VAD is a self balancing tree and each node in tree represent one range in process virtual memory.Each node has child in the form of left and right node.A node is represented using MMADDRESS_NODE struct...
