WannaCry Encryption Flow
Encryption Flow
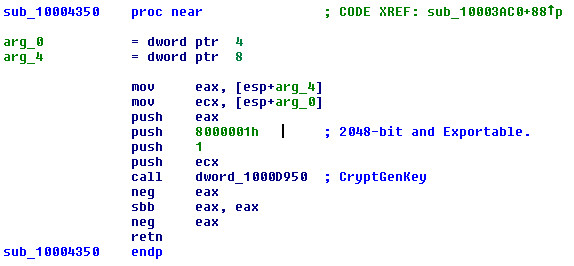
Generating RSA Key pair
Sample generates RSA public and private key pair and export
them to disk.
Public RSA key is written in file 00000000.pky and private RSA key is encrypted with another public
RSA key embedded in malware binary and written to file 00000000.eky.
Embedded Public RSA key in sample used to encrypt generated private RSA key.
File Enumeration
Enumerate Files in a Directory using Windows API’s FindFirstFile and FindNextFile.
Before encrypting file in a directory, malware checks for
list of directories and files to be excluded.
Directories to Exclude
File Extensions to Exclude
Exclude Files Dropped by Malware
File Types to Encrypt
File types to be encrypted is present as hard coded list in
malware binary.
Str2 is extension from hard coded list in malware binary.
Str1 is extension of the file to be checked against
hard coded list.
Key Generation
Random key at Run Time
If extension of the file is found in hard coded list then malware generates a Random key of size 0x10 (16) bytes using cryptography provider type 0x18(24) PROV_RSA_AES.
Random Key highlighted in red.
Encrypting Random Key
After performing operation on generated Random key which
will be later used to encrypt content of file, malware encrypts the Random key
with one public RSA key it has generated and written to file 00000000.pky.
After encryption the size of encrypted random key is 0x100(256)
bytes.
Encrypting File
Create New File
Malware creates a new file with name “original_file.old_extension.WNCRYT”.
Malware writes below information to the file created above.
- WANACRY! - Malware Magic Byte – 8 bytes
- ENCRYPTED RANDOM KEY LENGTH - 0x100(256) bytes.
- KEY BYTES - Encrypted Random key bytes of size in point 2.
- UNKNOW - dword value 0x4 - 4 bytes
- ORIGINAL FILE SIZE - 8
bytes
- DATA – Encrypted bytes of size in point 5
Encrypting Original file data and writing encrypted data to file “original_file.old_extension.WNCRYT”
Destination Buffer containing encrypted file content.
Encrypted file “original_file.old_extension.WNCRYT” content after encryption is
completed.
Set time of encrypted file to time of original file.
Moving encrypted file “original_file.old_extension.WNCRYT” to “original_file.old_extension.WNCRY”


















This is great observation. Similarly,if you want to encrypt your messages or want to prevent your conversation from the unauthorized access you may use an EnKryptonite app.
ReplyDeleteYou may download this app from:
https://goo.gl/3BvS1f and PlayStore https://goo.gl/EjBups
I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com or whatsapp: +1(213)785-1553
ReplyDeleteVery Fresh, Legit & Genuine Stuff available now
ReplyDeleteFreshly spammed from HIGH INCOME Databases
USA, UK, Canada States available
All info included SSN/SIN DOB DL
Fullz will be high credit scores 680 to 700+
Stuff will be fresh, never sold before
+92 3.1.7 2.7.2 1.1.2.2 WhatsApp/Tele-gram
7.5.2.8.2.2.0.4.0 I.C.Q
@peeterhacks Skype&WickrMe
exploit dot tools4u at gmail dot com
CC FULLZ with CVV's
DUMPS with Pins
Combos
Logs
Office365 Emails & Logs
Spamming Tools & Tutorials (SMTP's, RDP's, C-panels, Brutes, Scripting, etc)
Ha-cking stuff with complete tools, Guides, Ebooks & guidance
Carding fresh Methods, Loan Methods, Carding Cash-out Methods
Carding Tutorials, Transfers, top-up's
Kali Linux with Termex & Python
Keyloggers, Shells, RAT's
I.p's, Proxies, Server I.p's
Many other stuff we can provide on demand
Here we're
@killhacks ICQ&Tele.gram
+92 317272 1122 WhatsApp